C Programming: From Basic Syntax to Advanced Concepts
Dangling Pointer in C
Pointers are one of the most useful features in programming especially in languages such as C. And assembly Programming languages that offer pointers allow direct memory operation and that can be quite useful in several ways, including dynamic memory manipulation. But here, it does come with a great degree of accountability. Perhaps one of the most notorious evils that can crop up when using pointers is the naughty case of getting dangling pointers.
Well, here in this blog, we’ll go ahead and explore everything you need to know about dangling pointer in C. We will review the sources of each type, the dangers that come with them, and ways of avoiding them.
What Is a Pointer in C?
A pointer in C is a variable that holds or contains the address of another variable. Pointers are declared using the special operator called ‘ * ‘. For example:
int a = 10;
int *p = &a; // Pointer 'p' holds the address of variable 'a'
Pointer offers memory management, which includes dynamic storage, function parameter passing, and data structure such as lists among others. But this is dangerous, as misuse of pointers can result in subtle bugs or introductory-level security holes.
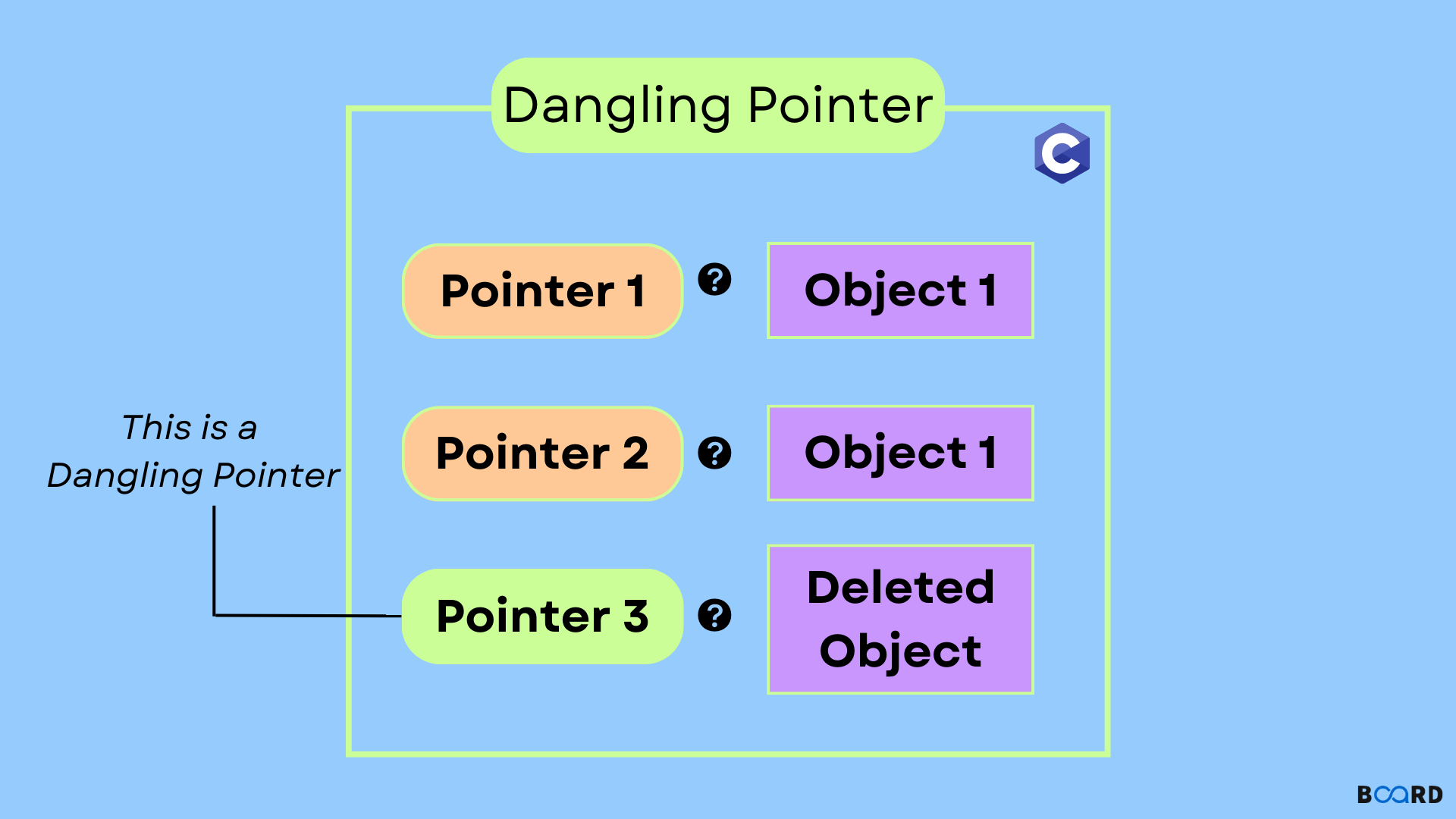
Understanding Dangling Pointer in C
A dangling pointer in C is a result of a pointer pointing at an address where data has been removed or the memory space has been released. Because the memory is no longer valid for use, as well as any attempt to access it, turns out to be undefined.
To explain this in more layman's terms, a dangling pointer ‘dangles’ in that it continues pointing to an invalid or an address that has no existence.
How Dangling Pointers Arise
Let’s examine some common scenarios where dangling pointers are created:
✅ Deallocation of Memory
In C, any pointer pointing to dynamically allocated memory when freeing using free(), becomes dangling until it is set to NULL.
#include <stdio.h>
#include <stdlib.h>
int main() {
int *ptr = (int *)malloc(sizeof(int)); // Dynamic memory allocation
*ptr = 42;
printf("Value: %d\n", *ptr);
free(ptr); // Memory is deallocated
// Undefined behavior (dangling pointer)
printf("Value after free: %d\n", *ptr);
return 0;
}
Why it Happens:
After the free(ptr) call, the memory that was pointed by the ptr becomes invalid. Getting to it results in undefined behavior.
✅ Returning Addresses of Local Variables
One of the errors that are often implemented is the return of the address of a local variable of a function. Once the function exits the local variable is out of its scope and it is then invalid and cannot be used again.
#include <stdio.h>
int *getLocalVariable() {
int x = 42; // Local variable
return &x; // Returning address of a local variable
}
int main() {
int *ptr = getLocalVariable();
// Undefined behavior (dangling pointer)
printf("Value: %d\n", *ptr);
return 0;
}
The storage needed for a parameter x is in the stack and any changes to it are erased once the function contains.
✅ Variable Scope Issues
Two more types of vulnerabilities that relate to buffers are the so-called ‘dangling pointers’ – which appear when pointers are still connecting to variables that have gone out of scope.
#include <stdio.h>
void testScope() {
int a = 100; // Local variable
int *ptr = &a;
printf("Value inside function: %d\n", *ptr);
}
int main() {
int *danglingPtr;
testScope(); // Variable 'a' goes out of scope
// danglingPtr now refers to invalid memory
return 0;
}
The lifetime of 'a' is terminated whenever the function exits which makes the pointer to go unwarranted.
Risks and Consequences of Dangling Pointer in C
Using dangling pointers can result in several problems:
- Undefined Behavior: If a pointer is dangling, that is, it points to an invalid memory location, using it may lead to errors, that result in producing undesired values or crash the program.
- Memory Corruption: Writing to dangling pointers can write a pointer to a memory location, one which doesn’t contain valid data any longer and makes it even more corrupted.
- Security Vulnerabilities: Dangling pointer vulnerabilities makes it easy for attackers to inject unauthorized code.
- Program Instability: Hanging pointers cause rather vague run-time errors that are usually hard to trace.
Examples of Dangling Pointer in C
Let’s analyze an example to demonstrate the Dangling pointer in C:
#include <stdio.h>
#include <stdlib.h>
void example() {
int *ptr = (int *)malloc(sizeof(int));
*ptr = 50;
free(ptr); // Memory freed
*ptr = 100; // Writing to dangling pointer (undefined behavior)
int *ptr2 = (int *)malloc(sizeof(int)); // Memory reallocated
// May print unexpected value
printf("Reallocated memory value: %d\n", *ptr2);
}
int main() {
example();
return 0;
}
Output:
Reallocated memory value: 100How to Avoid Dangling Pointer in C
✅Proper Memory Management
Special attention should be paid to pointers when freeing memory. Set pointers to NULL after deallocation:
free(ptr);
ptr = NULL;
✅ Using NULL or Sentinel Values
Nullifying a pointer ensures it doesn’t point to invalid memory:
if (ptr != NULL) {
free(ptr);
ptr = NULL;
}
✅Static Code Analysis Tools
You can use Valgrind or AddressSanitizer in order to identify all memory-related problems like dangling pointers.
Debugging Dangling Pointer Issues
- Using Debugging Tools
Valgrind: Indeed, it identifies memory leaks and invalid memory utilization.
GDB: The specific techniques to be addressed are - watchpoint and memory tracking for dangling pointers. - Analyzing Core Dumps
Dangling pointer in C accesses can also be localized using core dumps as a first-stage inference.
Best Practices for Safe Pointer Usage
- Follow RAII Principle: An acronym that stands for Resource Acquisition Is Initialization Automate memory management with a structure.
- Use Smart Pointers: Fortunately, in C++, we can use special automation elements like std::unique_ptr and std::shared_ptr to handle lifetimes.
- Avoid Returning Local Addresses: In every case, use dynamic allocation or static variables when you are returning pointers.
- Regularly Test with Tools: Moreover, memory debugging tools should be used often during the development.
- Document Pointer Ownership: Because dynamic memory allocation is dynamic, the ownership of the memory segment should also be described in detail in your programs.
Conclusion
It is seen that dangling pointers are one of the largest problems in C programs and yet with respect to understanding it and proper coding strategies, the risks posed can be kept under control. If you’re to adhere to the measures provided in this blog, it will be easier to write safer C code that is less vulnerable to attacks by hackers.
Always remember: A few general tips and a few pre-cautions will let you free from many hours of debugging blisters!
