Introduction to Computer Networking
Firewall Networking
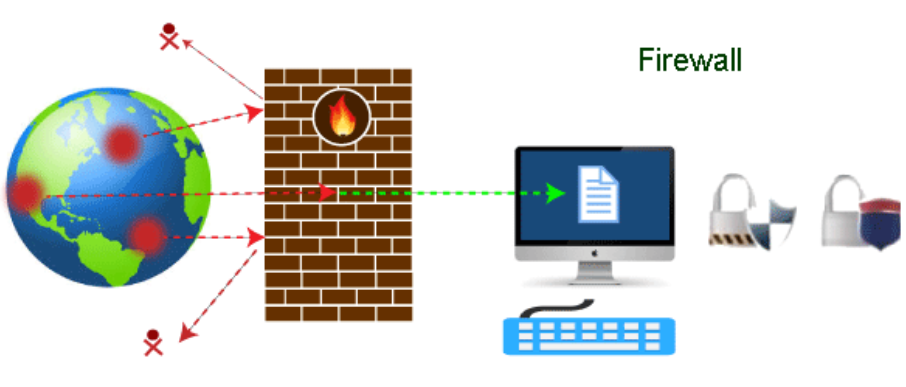
Introduction
Intranets in particular are protected by network firewalls, which are security tools intended to prevent or lessen illegal access to private networks connected to the Internet. Firewall policies specify the only traffic permitted on the network; all other traffic that tries to reach the web is prohibited. Network firewalls serve as a communications bridge between internal and external devices, sitting at the edge of a network.
Any data entering or leaving the network may be programmed to pass through a network firewall; it does this by inspecting each incoming message and rejecting those that do not fit the established security standards. When set up correctly, a firewall keeps away unauthorized users, hackers, viruses, worms, and other hazardous software from trying to enter the protected network while still enabling users to access whatever resources they require.
The topic of whether a firewall is a hardware or software is one of the most difficult to answer. As was already said, a firewall can be either a computer application or network security equipment. This indicates that the firewall is available on both the hardware and software levels, albeit it is recommended to have both.
Although a firewall can be implemented as hardware or software, both formats provide the same function. A hardware firewall is a real-world component that connects to a gateway and a computer network. For instance, a router for the broadband. A software firewall, on the other hand, is a straightforward application that is loaded on a computer and operates through installed software and port numbers.
Software vs Hardware Firewalls
Hardware firewalls
These firewalls can be purchased separately for business usage or, more frequently, come pre-installed in routers and other networking equipment. Any conventional security system and network design are thought to require them as a necessary component. Nearly all hardware firewalls provide a minimum of four network ports that permit connecting to several systems. A more comprehensive networking firewall solution is available for bigger networks.
Software firewalls
These are either installed on a computer or made available by the maker of an operating system or network device. They offer a lesser degree of control over functionality and security features and can be adjusted. A software firewall can defend against common control and access attempts, but it struggles to stop more complex network intrusions.
Types of Firewall
- Application-layer Firewalls
- Packet Filtering Firewalls
- Circuit-level Firewalls
- Proxy Server Firewalls
- Next-Generation Firewalls (NGFW)
- Stateful Firewalls
Working of a Firewall
The firewall is located at the intersection of the two networks ( i.e Private and Public networks). Typically, firewalls operate at OSI model layers 3 and 4. (i.e Network and Transport Layer repspectively). It analyses all incoming and outgoing communication, blocking any that does not adhere to the set security requirements ( i.e ACL ). ACL looks like this:
Importance of Firewall Networks
Firewalls are now so powerful, and they have a wide range of features and functions built-in
- Access Validation
- Record and Report on Events
- Hybrid Cloud Support
- Scalable Performance
- Network Traffic Management and Control
- Network Threat Prevention
- Application and Identity-Based Control
Firewall Restriction
- A firewall cannot shield a network against insider threats, backdoor assaults, or new infections.
- Ineffective network architecture and setup render the firewall useless.
- Antivirus and anti-malware software are not substitutes for a firewall.
- Threats from social engineering cannot be stopped by them.
- Password abuse is not prevented by a firewall.
- Attacks from a higher level of the protocol stack are not thwarted by a firewall.
- Attacks coming through dial-in connections, popular ports, or programs are not shielded by a firewall.
- They cannot comprehend tunneled traffic.
